Part 1: Key Global Cyber Trends, 2014-2022
Key Takeaways
As the scale of cyber attacks continues to increase, there’s a need for the private and public sectors to increase transparency and data-sharing related to cyber incidents. Better data would enable researchers to provide deeper insights into the patterns of criminal cyber activity that could help safeguard entities across various sectors of the economy.
The CISSM/GoTech Cyber Events Dataset attempts to collect data on publicly reported cyber events that have taken place since 2014 in an effort to determine trends in offensive cyber behavior and identify useful security-related implications.
These observations are useful for deciding how to prioritize scarce resources to protect the most vulnerable entities against the types of tactics commonly used by specific actors.
Introduction
The increasing reliance on digital technologies by state and non-state entities around the world may have contributed to greater productivity, yet it’s also opened up doors for various cyber actors seeking to take advantage of newly created cyber vulnerabilities. The United States has become increasingly concerned about the scale of cyber attacks on its domestic entities in light of this trend towards digitalization, which led to the 2020 Solarium Commission’s recommendation for a more comprehensive approach to cybersecurity. The Solarium Commission Report called for developing better defensive capabilities, increasing transparency, and building stronger international partnerships. It also emphasized the need for better reporting requirements for the private sector and recommended passing a national cyber incident reporting law.
Following the Report’s recommendations, President Biden signed a law in early 2022 that requires the Cybersecurity and Infrastructure Security Agency (CISA) to develop new reporting standards for entities involved in managing critical infrastructure. One of the goals of the regulation is to increase transparency and spot cyber trends across various sectors of the economy. The regulation asks the companies to provide “anonymized reports of cyber incident campaigns and trends, including, to the maximum extent practicable, related contextual information, cyber threat indicators, and defensive measures” for a broad set of actors, including security researchers.
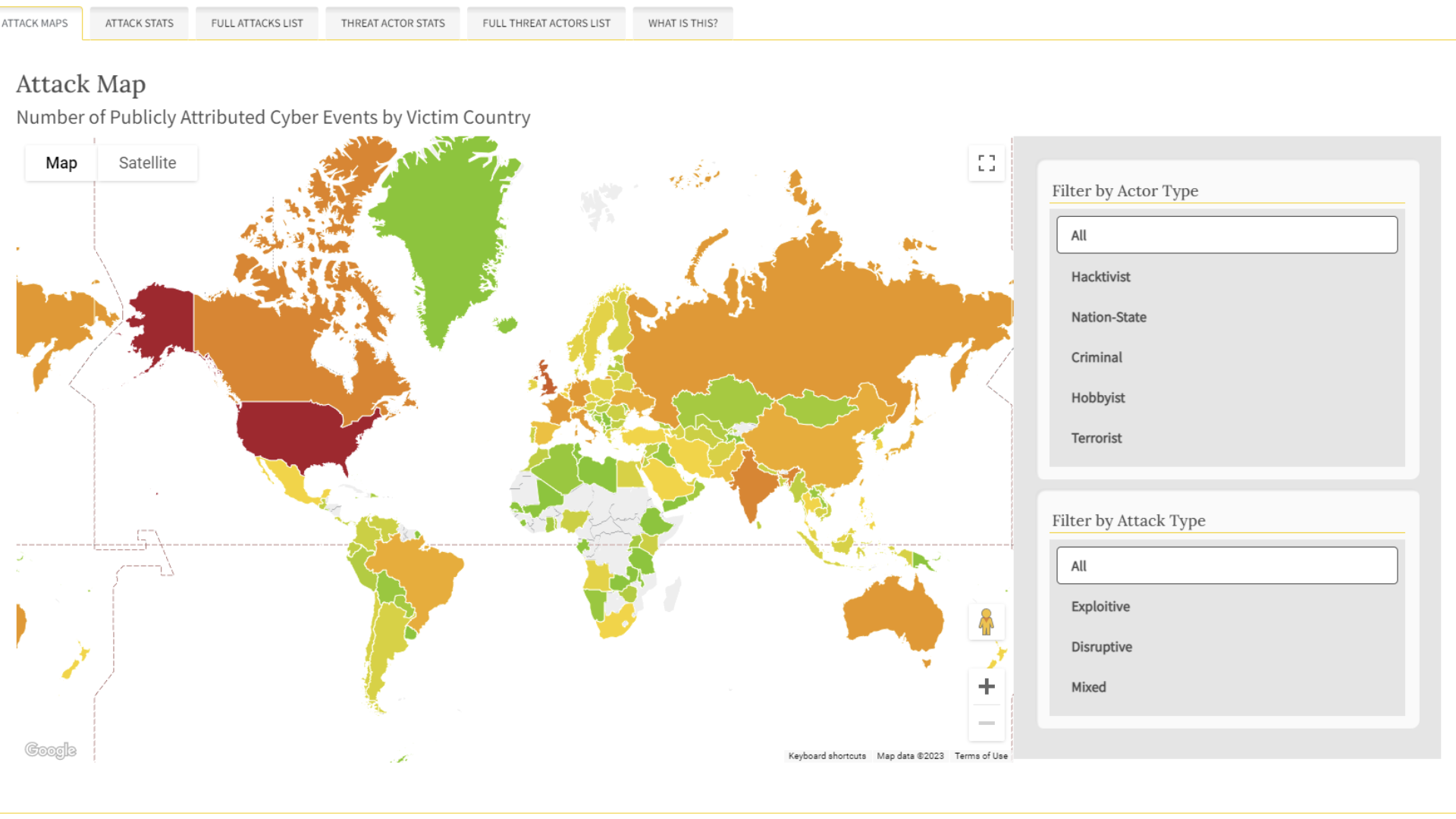
The CISSM/GoTech Cyber Events Database includes the types of data that the companies are being asked to share. The database contains information on attacks reported since 2014 and can be a powerful tool for analyzing various patterns related to criminal activity in cyberspace not only in the U.S. but across the entire world. The increased availability of such data is important for understanding cyber behavior and preventing similar attacks in the future. Looking at worldwide data is also helpful for countries that try to increase the resilience of their domestic industries. Identifying countries that see similar trends can be useful for fostering beneficial partnerships, while studying countries that manage to avoid a large number of attacks is useful for identifying best practices.
This is particularly important as cyber attacks increase in scale. Since 2014, the number of publicly known cyber attacks across the world has increased almost threefold (Chart 1). There’s a noticeable upward trend within this time period that’s likely related to increased digitalization as well as more stringent reporting requirements for enterprises. As businesses rely more and more on digital technology, storing growing amounts of data online and allowing employees to work remotely, the vulnerabilities to cyber attacks also grow. In recognition of these trends, policymakers feel the need to ensure that companies subject to such attacks remain transparent regarding the data and financial losses they incur.
Chart 1. Cyber Events Increasing in Scale, 2014-2022
2020 and 2022 saw the largest number of cyber attacks (Chart 1). This is likely due to the increased reliance on digital technologies after the onset of the COVID-19 pandemic in 2020 and the war in Ukraine in 2022. The former created more opportunities for malign actors to conduct cyber attacks while the latter increased the activity of nation-states that engaged in cyber ‘warfare’ as well as ‘hacktivist’ organizations that sought to create disruptions that would undermine Russia’s military actions.
Most of the cyber attacks reported were exploitative in nature, meaning their purpose was to steal data, intellectual property, or other types of sensitive information. These attacks are classified based on the part of an entity’s IT infrastructure that was exploited. By far, the most common exploitative attacks target application servers, followed by attacks that seek to exploit end hosts (through tactics like phishing) and sensors.
The second most prevalent type of attack - disruptive - seeks to disrupt the operations of an entity. Data attacks that manipulate, encrypt, or destroy data are most common, followed by message manipulation attacks that result in social media account takeovers or website defacements.
Understanding what type of attack is most likely in a given industry can help inform prioritizing resources to, for example, either secure sensitive data or improve response to disruptive attacks. Part 2 of this series analyzes key trends by sector, event type, actor type, motive, and geographic trends.